What anonymisation means – and what it doesn’t mean
The internet only works with data, and the data may be linked to an identity. There will never be an internet without data – so there will never be absolute anonymity, unbreakable for every potential adversary. Nevertheless, there are solutions that can make users practically anonymous. What all approaches have in common is that they try to hide a real identity under a pseudonym – and make it hard for adversaries to detect the real identity. To understand the core differences, we focus on VPNs and Tor.
VPN – Virtual Private Network
A VPN is probably the most common way to connect “anonymously” to the internet or to circumvent censorship. But how does it work? And does it really make you anonymous? Not really.
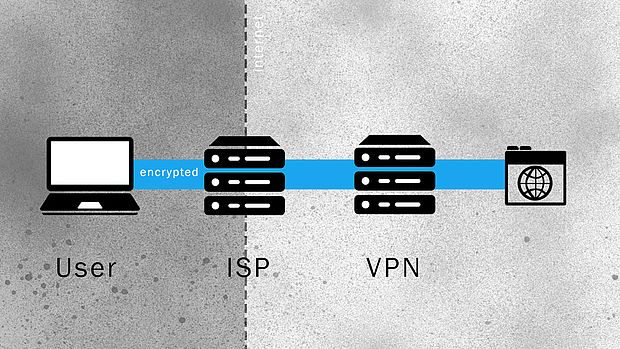
VPN stands for Virtual Private Network. While users regularly tell their Internet Service Providers (ISP) which website they want to access, they now tell their ISP that they want to be connected through a VPN. The VPN provider creates a tunnel between itself and the user to exclude the ISP from knowing what the user is doing on the internet. However, the fact that the user is connected to the VPN remains visible for the ISP.
An example: Given a User has internet access provided by their ISP and wants to open the website www.example.com.
A) Without a VPN, the ISP sees at least the IP address of the user and the address of the website www.example.com. So in most cases, the ISP knows the identity of the user and the website they access.
B) With a VPN, the ISP sees at least the IP address of the user and an IP address of the VPN provider. So in most cases, the ISP knows the identity of the user and that they are connected to a VPN, but not more. However, now the VPN provider knows the identity of the user and the website they access.
VPN: Pros and Cons
Pros: A VPN can help exclude the Internet Service Provider from tracking users’ behaviour. While ISPs are often nationally regulated and legally obliged to hand over data to governments, this may differ for a VPN. Some providers may be based in countries that do not legally cooperate with your state-level adversaries. Secondly, a VPN can help circumvent censorship. As the ISP is excluded, it cannot prevent you from accessing a blocked website any more.
Cons: Users have to trust a VPN provider in that it really does what it claims to do. While users don’t have to trust their ISPs anymore, the “all-knowing entity” is now the VPN. Secondly, a VPN provider may also be legally bound to hand over certain data. Users should check this in advance. Thirdly, especially free VPN providers may earn money with users data. As they are the “all knowing entity”, they may record users behaviour and make money with this data. Lastly, only by using a VPN, users could look suspicious in certain countries and contexts.
Tor – The Onion Routing
Tor is the biggest and best known network to anonymise users’ online behaviour. It stands for The Onion Routing. It is developed by the Tor Project with developers all over the world. It is a decentralised network which means that Tor servers are based all over the world and everybody could contribute with a Tor server. Reporters Without Borders also operates two servers. To connect to it, users have to download and install the freely available Tor browser. How does it work?
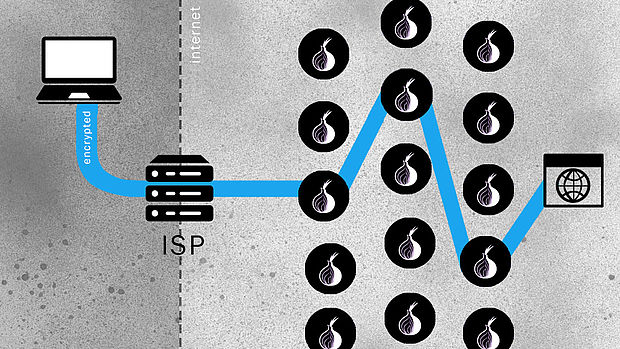
While users regularly tell their Internet Service Providers (ISP) which website they want to access, they now tell their ISP that they want to be connected to the Tor network. The traffic is encrypted in transport and is then routed through the Tor network over three Tor servers. The idea is that none of the servers sees both the IP address of the user and that of the website. So neither the ISP nor Tor itself knows what users do on the internet. Also, as the system chooses randomly three servers out of around 7000 Tor servers in total, it is almost impossible to detect which way a user’s connection takes through the network. The more people use Tor, the better is the anonymity for everybody.
To get the Tor Browser, please check the website of the Tor project and also have a look on the FAQ to not make mistakes that compromise your anonymity.
Tor: Pros & Cons
Pros: Tor can help exclude the Internet Service Provider from tracking users behaviour. While ISPs are often nationally regulated and legally obliged to hand over data to governments, Tor is global, decentralised network that cannot be easily regulated by single states. By default, Tor does not store any user data, so Tor cannot even provide data if it was legally obliged to do so. Secondly, Tor can help circumvent censorship. As the ISP is excluded, it cannot prevent you from accessing a blocked website any more. Even if the access to Tor itself blocked, the network offers a special way to circumvent that with its “bridges”.
Cons: Just by using Tor, users could look suspicious in certain countries and contexts. Also, the access to Tor can sometimes be blocked by national ISPs (see how to circumvent that here) and the speed of the internet connection is usually a bit slower than without Tor.
Tor - Onion Services
The best use of Tor is probably to browse the internet anonymously. However, Tor can do more. There are also so-called Onion Services that host websites in the Tor network itself. So Tor is not ‘only’ a bridge in the regular web, but also the destination of a connection. Why is that useful?
People who operate an Onion Service do not necessarily have to reveal their identity and information about the location of the Onion Service. Therefore, nobody can force them to delete certain information. Tor Onion Services are resistant against censorship and guarantee anonymity for both its operators and visitors.
For journalists, they may be relevant to share files anonymously (e.g. over Onion Share) or to set up an anonymous post box for whistleblowers (e.g. over Secure Drop).